
ACL Digital
5 Minutes read
Hardware-Level Security for Embedded Devices: Protecting Systems from Silicon to Cloud
The rapid proliferation of IoT and connected embedded systems in sectors such as industrial automation, healthcare, automotive, and consumer electronics has redefined performance expectations, but it has also expanded the attack surface far beyond the software layer. Modern threat actors are no longer confined to exploiting vulnerabilities in applications or firmware; they increasingly target the silicon itself through methods like side-channel attacks, hardware fault injection, and physical tampering. Once compromised at the hardware level, devices can be cloned, reprogrammed, or hijacked with a persistence that software patches alone cannot counter. This shift makes hardware-level security, embedding trust anchors directly into the chip architecture, a critical design priority, ensuring that integrity, authentication, and confidentiality are enforced from the moment the device powers on.
Understanding Hardware-Level Security
At its core, hardware-level security means building protection right into the physical chips and components of an embedded device. Unlike software-based security, which depends on applications, operating systems, and patches that can be bypassed, hardware security creates a permanent, tamper-resistant foundation. Even if higher-level software is compromised, the security baked into the silicon itself keeps the device protected and trustworthy.
Key elements include:
- Secure Boot: Verifies that only trusted firmware runs when the device powers on, blocking malicious code before it even has a chance to load. Additionally, in advanced designs, the secure boot chain starts from immutable ROM code and extends to secondary loaders using cryptographic signatures (e.g., SHA-256 + ECDSA/Ed25519), ensuring rollback protection and anti-replay mechanisms.
- Hardware Root of Trust (RoT): Acts as the device’s cryptographic anchor, enabling secure identity, authentication, and encryption key generation directly within the silicon. Modern RoT implementations leverage physically isolated storage, and increasingly, Physically Unclonable Functions (PUFs) to derive device-unique keys without storing them in NVM.
- Physical Tamper Resistance: Detects and reacts to invasive attacks such as probing or glitching, often by erasing sensitive data to ensure nothing valuable can be stolen. PCB-level techniques such as buried traces, routed internal security lines, and epoxy encapsulation further complicate invasive probing attempts.
- Secure Key Storage: Keeps encryption keys locked away in isolated hardware modules, making them unreachable to attackers, even if they exploit software vulnerabilities. Keys are injected via secure provisioning workflows using HSMs, encrypted channels, and OTP/eFuse memory, preventing unauthorized extraction even during manufacturing.
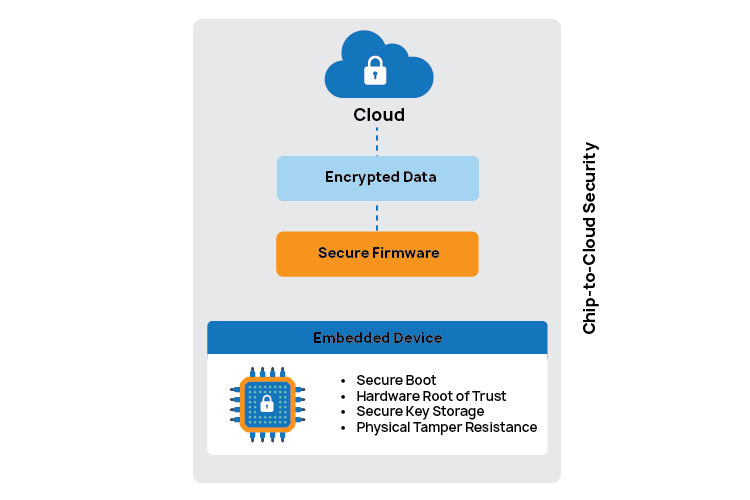
Threat Landscape: Risks to Embedded Devices
As embedded systems evolve in capability, their exposure to sophisticated hardware-level attacks grows proportionally. These threats often exploit physical access, electrical behavior, or firmware weaknesses, bypassing traditional software defenses entirely. Key risks include:
- Side-Channel Attacks (SCAs): Exploiting electromagnetic emissions, power consumption patterns, or timing variations to extract sensitive cryptographic keys without altering the device’s operation.
- Fault Injection Attacks: Voltage or clock glitching used to skip checks or force invalid states. Mitigated through on-chip voltage/clock monitors, glitch detectors, redundant execution paths, and secure watchdogs.
- Firmware Tampering: Injecting or modifying low-level firmware to create persistent backdoors, disable security checks, or gain full control over device functionality.
- Physical Intrusion: Direct manipulation of circuit boards or debug interfaces (e.g., JTAG, SWD) to bypass authentication, extract data, or clone device architectures.
- Real-World Breaches: Incidents such as payment terminals compromised via chip probing or connected medical devices altered through firmware modification have demonstrated how hardware-level exploits can cause operational shutdowns, regulatory violations, and public safety risks.
- Business Impact: Beyond data loss, a compromised embedded device can disrupt safety-critical operations, damage brand trust, and trigger costly recalls—turning a single vulnerability into a large-scale business continuity threat.
Benefits of Hardware-Level Security in Embedded Systems
Implementing security at the silicon level not only fortifies an embedded device against direct hardware exploits but also creates a resilient foundation that safeguards the entire operational ecosystem. The advantages extend beyond threat mitigation, delivering measurable business, operational, and compliance gains:
- End-to-End Trust from Chip to Cloud: Hardware-based trust anchors ensure that every transaction, data packet, and control signal is cryptographically validated from the point of origin in the chip to its destination in the cloud, eliminating the possibility of man-in-the-middle or spoofing attacks.
- Enhanced Protection Against Cloning and Counterfeiting: Unique, hardware-bound device identities and cryptographic key storage make it virtually impossible to replicate or counterfeit devices, protecting intellectual property and preventing unauthorized hardware from entering the supply chain.
- Long-Term Device Lifecycle Security: Embedded hardware security enables secure Over-the-Air (OTA) updates with firmware integrity checks, ensuring that devices remain protected against evolving threats throughout their operational lifespan without requiring physical recalls.
- Regulatory and Industry Compliance: Hardware security features help manufacturers meet stringent standards such as IEC 62443 for industrial control systems and NIST guidelines for cryptographic assurance, reducing certification timeframes and avoiding costly non-compliance penalties.
Best Practices for Implementing Hardware-Level Security
Securing embedded devices isn’t something that can be added at the end, it has to be built into the design from day one. The following practices help ensure that devices remain protected throughout their lifecycle:
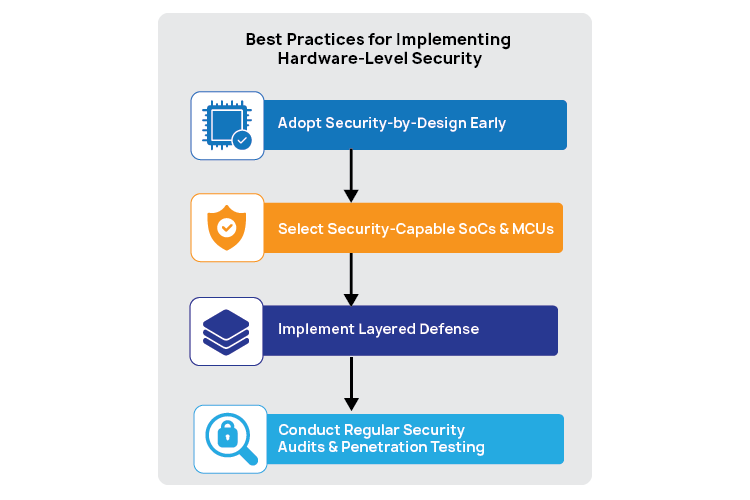
- Start with Security-by-Design: Plan for security at the prototyping stage itself. Features like secure boot and controlled access to debug interfaces should be part of the initial design, not added later. Design PCB layouts with EMI shielding, isolated secure domains, and secure routing for sensitive nets.
- Choose the Right SoCs/MCUs: Use processors designed with built-in security features such as ARM TrustZone, secure enclaves, random number generators, and tamper detection. These hardware-level protections reduce reliance on software alone. Platforms like ARM Cortex-M33 with TrustZone-M, STM32 TrustZone/CRYP engines, and NXP HAB bring hardware-accelerated cryptography, tamper pins, and secure key ladders.
- Build a Layered Defense: Combine hardware security with secure firmware and encrypted cloud connections. This ensures devices are protected at every level from chip to cloud with features like secure key storage, signed firmware updates, and encrypted data transfer. Incorporate instruction-integrity protections like CFI, stack canaries, and secure watchdog supervisors to detect runtime anomalies.
- Test and Validate Regularly: Run security audits and penetration tests to identify vulnerabilities before attackers do. This includes validating hardware interfaces, firmware update paths, and potential side-channel leakage points. Perform side-channel resistance tests, secure firmware-pipeline audits, and real-time attestation checks for field-deployed devices. For production deployments, extend identity management with X.509 certificates or blockchain-based integrity logs to support zero-trust provisioning and secure lifecycle tracking.
Platform-Specific Security Features
| Platform | Security Features |
| ARM Cortex-M/A | TrustZone-M, CryptoCell, MPU, secure debug lock |
| STM32 | Secure boot, CRYP engine, OTP memory, tamper pins |
| NXP i.MX | High Assurance Boot (HAB), CAAM, secure JTAG |
| TI Sitara | Secure boot, PRU isolation, secure key storage |
| Microchip SAM | TrustZone, secure element integration, tamper detection |
How ACL Digital Strengthens Embedded Devices with Hardware-Level Security
ACL Digital combines deep semiconductor knowledge and domain experience to design secure embedded solutions that safeguard devices from silicon to cloud. With proven expertise across healthcare, industrial, automotive, and consumer electronics, we ensure device integrity, compliance, and resilience.
- Secure Design & Bootloaders: Experience in MCU/SoC security integration and authenticated boot processes, deployed in safety-critical medical and industrial devices. Implemented ROM-anchored secure bootflows with AES-GCM firmware decryption and anti-rollback counters for critical industrial and medical devices.
- Hardware Root of Trust: Implemented cryptographic key management and secure provisioning across ARM TrustZone and STM32 platforms, enabling trusted OTA updates and device authentication.
- TPMs & Secure Elements: Delivered TPM-based identity management and hardware-isolated key protection for automotive and connected IoT solutions. Integrated eFuse/OTP key storage and secure JTAG lockout with attestation certificates for automotive-grade platforms.
- Secure IoT Gateways: Designed gateways with tamper resistance, intrusion detection, and encrypted cloud connectivity (AWS, Azure or GCP) for industrial IoT ecosystems.
- Applied Innovation: Built a secure Linux-based ML solution with Time-of-Flight cameras, integrating hardware encryption and secure firmware pipelines for real-time analytics. ToF ML edge devices used isolated crypto engines and DMA-based hashing to validate executable integrity in real-time.
- Platform Expertise: Strong track record with ARM, NXP, STM32, Microchip, and TI, tailoring silicon security features to customer-specific use cases.
By embedding trust at the hardware level, ACL Digital helps OEMs deliver future-ready, secure, and compliant devices that withstand today’s cyber-physical threats.
Reach out to our experts to learn how ACL Digital ensures robust, hardware-level security across embedded and IoT devices.




