

ACL Digital
5 Minutes read
Chip-to-Cloud Security: Ensuring End-to-End Protection in Digital Ecosystems
The explosion of connected devices from smart appliances to autonomous vehicles, combined with hybrid work and increasing edge deployments has dramatically expanded the attack surface for modern enterprises. Cybercriminals are no longer just targeting data centers or cloud apps; they’re exploiting vulnerabilities at the hardware level, device firmware, and in the communication chain between edge and cloud.
Chip-to-Cloud security is a modern, layered approach that ensures protection from the silicon level all the way to the cloud infrastructure. Unlike traditional models that secure isolated endpoints or rely solely on software-level defenses, Chip-to-Cloud integrates secure hardware, encrypted communication, and cloud-based monitoring to deliver end-to-end trust.
While many devices are secure in isolation, the real risk lies in how they interact within the broader ecosystem through unsecured networks, compromised firmware, or weak identity management. This blog explores how organizations can close that security gap by adopting a security-first design approach that anchors trust across every layer, from chip to cloud.
Securing the Edge: Protection at the Chip Level
As threat actors shift their focus to device-level vulnerabilities, the foundation of security must begin where data is born at the chip. Hardware-based security elements like Trusted Platform Modules (TPM), Hardware Security Modules (HSM), and secure microcontrollers play a critical role in establishing device identity, safeguarding cryptographic keys, and ensuring data integrity from the moment it’s captured.
To protect sensitive workloads at the edge, Trusted Execution Environments (TEEs) isolate code and data in secure enclaves, preventing unauthorized access even from compromised operating systems. TEEs ensure that only verified, authenticated processes can access protected memory regions, making them essential for secure boot, firmware validation, and runtime attestation.
However, edge devices face unique constraints: limited compute resources, physical exposure, and diverse hardware architectures. These factors make them more susceptible to tampering and side-channel attacks. Implementing a robust chip-level security stack not only mitigates these risks but also establishes the root of trust required for any end-to-end security model.
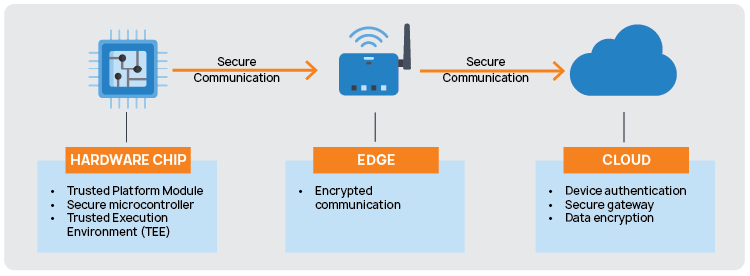
Securing Data in Transit: Encryption and Communication Integrity
- Criticality of Encryption Across the Pipeline: As data moves from the chip through edge nodes to the cloud, it becomes vulnerable to interception, manipulation, or replay attacks. Ensuring secure communication in transit is non-negotiable for preserving data integrity, confidentiality, and authenticity across this entire path.
- Encryption Between Chip, Edge, and Cloud Layers: Communication channels between hardware endpoints (chips), edge gateways, and cloud platforms must be encrypted by default. This includes:
- Chip-to-edge communication over interfaces like I2C, SPI, or UART, where lightweight encryption schemes or hardware-backed cryptographic engines are used.
- Edge-to-cloud interactions typically leverage IP-based secure transport protocols.
- Key Technologies Enabling Secure Data Transit:
- TLS 1.3 (Transport Layer Security): The standard protocol for encrypting edge-to-cloud communication, offering forward secrecy and reduced handshake latency.
- DTLS (Datagram TLS): Optimized for UDP-based protocols common in IoT and constrained networks.
- VPNs (Virtual Private Networks): Used in private mesh networks or device clusters for establishing secure tunnels over public infrastructure.
- MQTT over TLS: Common in IoT messaging, MQTT is secured using TLS to protect telemetry data and device commands.
- IPSec & Secure CoAP: Adopted in resource-constrained devices with IP-based communication.
- Encryption Key Management:
- Devices must securely generate, store, and rotate encryption keys using hardware-based key vaults such as TPMs or Secure Elements (SEs).
- Use of asymmetric key infrastructure (PKI) and X.509 certificates for device authentication and mutual TLS handshake.
- Integration with cloud-based Key Management Services (KMS) like AWS KMS or Azure Key Vault for secure key lifecycle operations, provisioning, usage tracking, rotation, and revocation.
- Managing Data Privacy at Scale:
- Enforcing end-to-end encryption with no intermediate decryption along the route.
- Applying encryption policy controls based on sensitivity levels, region-specific compliance (e.g., GDPR, HIPAA), and service-level agreements.
- Leveraging zero-trust network architectures, ensuring encrypted communication even within trusted environments.
Cloud Security: Protecting Data in the Cloud Ecosystem
Cloud platforms rely on a layered security approach using tools like Identity and Access Management (IAM), encryption frameworks, and centralized monitoring to protect data at rest, in use, and in motion:
- Encryption for Data at Rest and in Use: Strong encryption protocols (AES-256, envelope encryption) are applied to data stored in object storage, databases, and block volumes. Confidential computing is increasingly used to protect data in memory during execution, ensuring zero exposure even to cloud providers.
- Vulnerabilities Between Chip and Cloud: Data moving from edge to cloud remains vulnerable to leakage, man-in-the-middle attacks, or unauthorized access if not adequately governed. Insecure APIs, weak device authentication, and misconfigured permissions are common exploit points in this transition.
- Continuous Monitoring and Detection: Cloud-native security tools like AWS GuardDuty, Azure Defender, or Google Chronicle are essential for real-time threat detection. These tools leverage behavioral analytics, log correlation, and anomaly detection to identify suspicious activity early.
- Compliance-Centric Cloud Security: Enterprises must align with compliance frameworks such as ISO/IEC 27001, SOC 2, GDPR, or HIPAA by enforcing audit trails, access controls, and encryption standards. Cloud security postures should be continuously evaluated using tools like CSPM (Cloud Security Posture Management) to maintain regulatory readiness.
- Zero Trust and Micro-Segmentation: In a modern chip-to-cloud model, trust boundaries must extend beyond the network perimeter. Zero Trust Architecture (ZTA) ensures all access is authenticated and authorized, while micro-segmentation prevents lateral movement within cloud environments.
- Secure Integration with Edge and Device Layers: To maintain a unified security fabric, cloud platforms must integrate with hardware-based identity mechanisms and secure edge attestation protocols. This enables end-to-end visibility and policy enforcement from the physical device up to the application layer.
- Operationalizing Cloud Security at Scale: Automation is critical, security as code practices (e.g., using Terraform or CloudFormation with security modules) allow consistent, repeatable deployment of security controls across multi-cloud environments. Integration with DevSecOps pipelines ensures that security is embedded early in the application lifecycle.
- Risk of Cloud Misconfiguration: Misconfigured cloud buckets, open ports, or overly permissive IAM roles can expose enterprise data. Cloud configuration must be continuously validated through automated audits, security baselines, and drift detection tools.
- Security Beyond Infrastructure: True chip-to-cloud protection also extends to SaaS services, APIs, and data lakes hosted in the cloud. Security teams must manage API gateways, enforce OAuth 2.0 scopes, and audit service-to-service communication to prevent privilege escalation and data exfiltration.
The Future of Chip-to-Cloud Security: Trends and Innovations
- AI-Driven Threat Detection: Security systems are increasingly integrating AI/ML to identify anomalies in real-time across the chip-to-cloud stack, enabling predictive defense mechanisms instead of reactive alerts.
- Quantum-Safe Encryption: With quantum computing on the horizon, businesses are beginning to adopt post-quantum cryptographic algorithms to protect data at rest and in motion against future threats.
- Edge AI Security: Running AI models locally on edge devices requires secure inferencing and protected model execution within Trusted Execution Environments (TEEs) to prevent intellectual property theft and inference tampering.
- Zero Trust Architecture Integration: Modern chip-to-cloud strategies incorporate Zero Trust principles, validating identity and enforcing least privilege at every access point, including hardware, edge gateways, and cloud APIs.
- Decentralized Identity and Secure Provisioning: Decentralized device identity frameworks and secure provisioning mechanisms are gaining adoption to ensure tamper-proof onboarding and continuous attestation across device lifecycles.
- Confidential Computing and Encrypted Execution: Confidential computing frameworks enable processing of encrypted data without exposing it in memory, securing sensitive operations in the cloud and edge environments.
- Security as Code and DevSecOps Alignment: Security policies are being embedded as code within CI/CD pipelines, allowing continuous security posture management and automated remediation across firmware, edge software, and cloud infrastructure.
- Future-Proofing Through Interoperable Standards: Adoption of open standards like Matter, PSA Certified, and Project CHIP helps ensure cross-vendor compatibility and long-term security viability for rapidly evolving ecosystems.
- Digital Twin-Based Threat Modeling: Simulating security events using digital twins of chip-to-cloud systems allows organizations to test responses, validate policies, and reduce real-world risk exposure.
- Strategic Imperative for Enterprises: To stay resilient, enterprises must embed these innovations early in the architecture, moving from reactive patching to proactive, policy-driven, and hardware-backed security models.
About ACL Digital
As digital ecosystems grow more complex, the need for a comprehensive, chip-to-cloud security strategy has never been greater. Isolated protections are no longer sufficient, security must be embedded across the entire stack, from silicon to cloud services. By implementing hardware-based root of trust, encrypted data pipelines, zero trust architecture, and continuous threat detection, businesses can ensure end-to-end protection, reduce vulnerabilities, and maintain regulatory compliance.
At ACL Digital, we help businesses implement end-to-end security architectures tailored to their connected ecosystems. Our expertise spans secure hardware integration, trusted execution environments, secure firmware development, cloud-native security, and zero-trust implementation. Whether you’re building IoT platforms, edge devices, or cloud-connected solutions, we ensure your infrastructure is protected at every level—from chip to cloud.
Partner with ACL Digital to design and deploy a resilient chip-to-cloud security framework tailored to your ecosystem, contact us to connect with our experts.
Related Insights



Top 5 Hard Truths About Your Governance Strategy

ETL Simplified: Storing and Transforming Data Fully Inside Databricks


