

Shobhit Sharma
4 Minutes read
Generative AI in DevOps: An Effective Tool for Accelerating Workflows
The Cybersecurity has become one of the major concerns for all businesses as the exposure to threats and risks are getting bigger day by day. Data is sacrosanct for every organization. The traditional Cybersecurity measures are not evolving fast enough to withstand the onslaught of new-age cyber threats. Organizations must look beyond the traditionally available IT security approach and look for ways to incorporate intelligent analytics such as Big data and others into their Cybersecurity strategy.
Many companies look at Cybersecurity from a technical point of view rather than a business point of view and as a result more often than not, the companies get the wrong idea about how to construct a Cybersecurity model. In a recent survey on Cybersecurity-management maturity, almost 80% of the surveyed executives reported that their companies don’t have enough countermeasures to guard against the Cybersecurity threats.
The study also shows that only 5% of the surveyed organizations have mature Cybersecurity infrastructure in place.
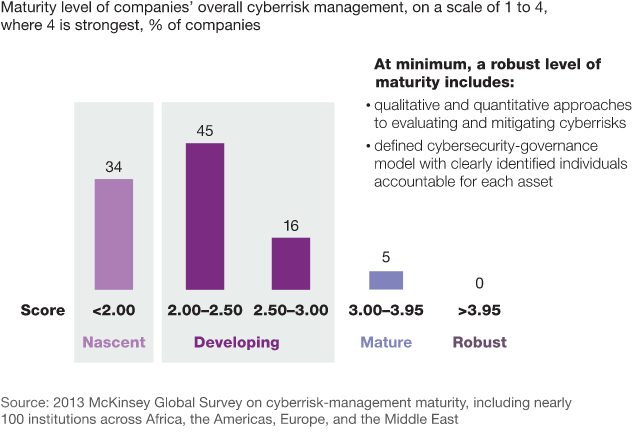
The overarching situation demands a new perspective on how we view security.
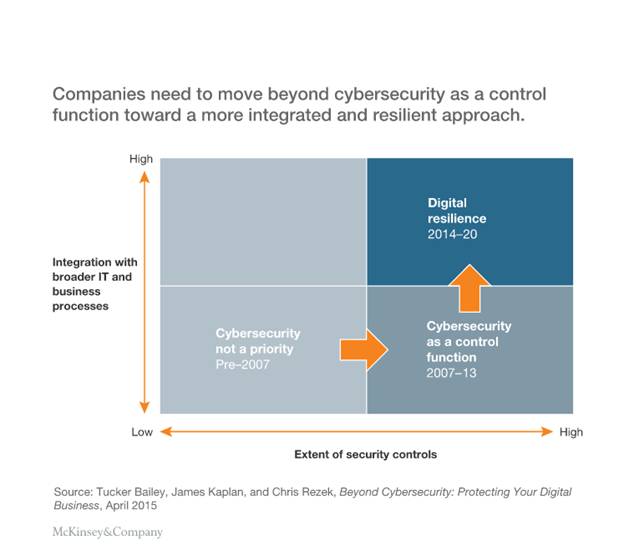
Mckinsey introduced a new Cybersecurity model called Digital resilience. As per the Digital resilience model, the companies should design customer applications, build business processes and technology architectures keeping Cybersecurity at the nucleus. The traditional security outlook of security in Silos is now obsolete. The evolving security scenario demands the focus be put on individual processes like intrusion detection, I&AM, data protection, incident response, and the like combined to protect the sensitive Customer and Company information.
As shown in the matrix below, the Cybersecurity will become more prominent with the passage of time.
Now let’s look at the ways in which the analytics can help to build a strong Cybersecurity model. Companies these days have a large amount of data, be it operational or historical, and to deal with such huge databases Big data comes into play. Artificial Intelligence/Machine Learning models combined with Big data and Data Analytics will play a major role in stopping cyber criminals from accessing critical information.
A holistic Cybersecurity approach to every business process and the organization culture will enable the enterprises to assess both external and internal threats, helping them to see a bigger picture of threats against their enterprises.
What’s new in Cybersecurity
Going forward, Big data will have an impact that will change most of the product categories in the field of computer security including solutions, network monitoring, authentication and authorization of Users, IAM, fraud detection & Prevention, Systems of Governance and Risk & Compliance. Big data will also usher a new era of security controls as regular firewalls, the anti-malware solution can’t cope up with the ever-increasing security challenges. With the introduction of AI, the tools of data analysis have evolved further to enable a number of advanced predictive capabilities and robotic process automation.
Conclusion
To conclude, the organizations should look for a holistic Cybersecurity strategy tailored to target the threats and the risks specific to the requirements and demands of their organization. Big data requires the collection of information from multiple sources and in different formats/types. A logical way forward is to have a single architecture to collect, index, normalize, analyze and share all the information, and organization should look to profile accounts, users or other entities, and look for anomalous transactions against those profiles.
Organizations should ensure that the continued investment in security products promotes technologies that are based on approaches to agile-based analysis rather than static signature-based tools to threats.
Related Insights

