

Madhushree Bharati
June 13, 2018
2 Minutes read
SS7 Vulnerabilities and Our Solution
The SS7 (Signalling System 7) network was created decades ago when only government telco companies were connected to it. People were untrained and were not aware of its being, its uses and how it could be exploited.
So, no protection was required for this protocol. But today in the world of network attackers, these vulnerabilities need to be properly taken care of. Without proper actions against these vulnerabilities, the user’s mobile devices easily get exposed to hacking attacks.
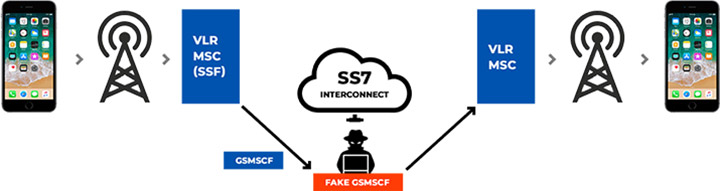
Attacks caused by SS7 Vulnerabilities:
- Daniel of Service Attack: A DoS is an attack where the attacker shuts down the entire network making it inaccessible to all its users.
- Geolocation: A SS7 attacker can find out the exact location of a user by knowing only the phone number.
- Call Interception: The attacker routes the call to its own system, bridges the call to the other party and then records the conversation without the knowledge of the subscriber or the operator.
- Payment Scam: Here the attacker makes use of some Unstructured Supplementary Service Data(USSD) codes. The attacker transfers money via the USSD codes from the user’s account and proceeds with call deletion, without the subscriber’s knowledge.
- The Discount SMS scams: Attacker uses a mobile operators’ network to transmit a huge amount of wholesale SMS messages. Some of these exercises continue for years undetected. Mobile operators use SMS firewalls to defend their networks from such attacks. First-generation firewalls can yet be evaded by smart attackers.
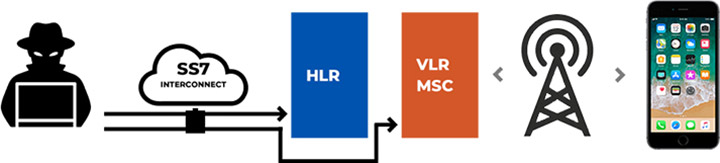
Our Solution
ACL Digital SS7 Solutions can help you lessen your country’s cellular network risks from SS7 vulnerabilities.
- Oversight Detect: It includes a passive network tap connection that performs continuous investigation of all protocol data and alarms for the logging of events.
- Oversight Protect: It offers protection to the carrier’s cellular network by providing a dynamic cellular firewall.
- Oversight Penetration Testing SS7 Vulnerabilities: It allows the carrier to detect the extent to what its network elements (HLR, VLR/MSC, SGSN) are helpless to the SS7 attacks.
Our solutions are economic and reduces unknown SS7 traffic requests providing your carrier with safe networks.


