Zero Trust Network Access (ZTNA) Solution

Overview
A $100 mn Technology startup, the Client builds cloud managed network services platform, which is fully activated and managed from the SASE cloud.
The key areas worked upon include:
- Cloud Enabled Mobile work force
- Secure VPN access to BYOD users
- Easy access to Connectivity layer from any Location
Download Case Study
Challenges
Remote access VPN used by mobile users was experiencing latency while accessing the applications
Traditional remote access VPN backhauling the traffic to reach the cloud
Client wanted to host all the Network services in the Cloud by virtualizing the appliances and developing MDM tools for the BYOD users
Solution
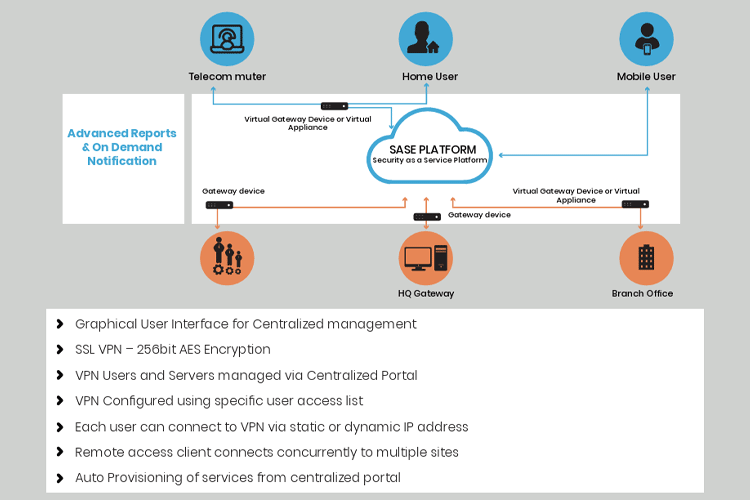
- Centralized cloud based (SASE) Network Security services for users at Branch and Corporate offices
- Virtual appliances (Firewall, VPN, Content filtering and IDS/IPS) Hosted in the SASE cloud
- Developed MDM application for BYOD and remote access users
- Enabled secure access to SaaS applications from unmanaged devices with inline protection by using SAML proxy integration
- Established Secure Access to Private and public cloud and applications hosted at the Datacenters
Outcomes
- Cloud-delivered security infrastructure
- Enablement of secure access to all applications, and maintain full visibility and inspection of traffic across all ports and protocols
- An architecture designed to secure access to all applications with the protection against cyber attacks









